Informatica Data Masking Solution– A Data Security Product (Dynamic Data Masking) for Structured Data Masking

Have you ever tried to read out a credit card number from your credit card statement? You can’t. Give it a try. Why did we fail to read 16-digit numbers from our own statement? Because the statement report has obscured some or all of the 16 digits.
In the data security world, the mechanism of obscuring or hiding original data is termed Data Masking. The main agenda of this post is to familiarize the audience with Dynamic Data Masking (DDM) – a niche data security product for masking structured data (stored in a relational database like Oracle, DB2, etc.).
Introduction: - DDM is a lightweight, high performance, easy to install and no configuration required data masking product for Windows / Linux/ UNIX systems. Just few clicks are required for installation and you are ready to GO. DDM provides rules driven by masking facility and comes with a highly intuitive administrative window to configure rules that need to be applied to provide fictitious data to unauthorized users. At a high level, DDM is positioned between the original data resource and the client, and fictitious results are obtained by the client based on rules configured in DDM.
High level overview: - DDM intercepts an incoming request and modifies it based on a configured rule set. Rule sets are modifiers which are configured by a privileged user (administrator) and they alter the request by using a pattern matching algorithm. The modified request is then sent to the database. The database processes this query and executes it as it is coming from the application directly. 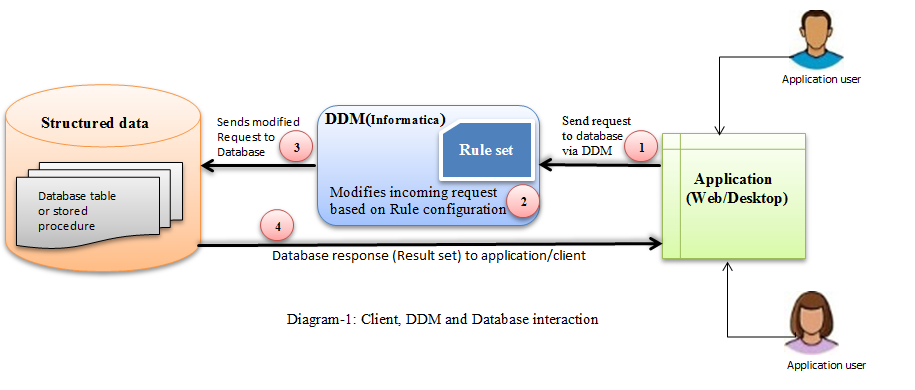 Let’s walk through the above diagram (Diagram-1) to understand the flow of events. The application user sends the request to the database through DDM. Once the incoming request is intercepted by DDM, it matches the request with configured rule sets and modifies it accordingly if a match is found. After DDM applies matched rules, it forwards the request to the database and the database executes the incoming request and sends the response back to the application user directly. For application users, DDM is just a gateway to pass the database request through and the application user cannot differentiate whether it is connecting to the database directly or through DDM.
Let’s walk through the above diagram (Diagram-1) to understand the flow of events. The application user sends the request to the database through DDM. Once the incoming request is intercepted by DDM, it matches the request with configured rule sets and modifies it accordingly if a match is found. After DDM applies matched rules, it forwards the request to the database and the database executes the incoming request and sends the response back to the application user directly. For application users, DDM is just a gateway to pass the database request through and the application user cannot differentiate whether it is connecting to the database directly or through DDM.
Where DDM finds its usage: Do you have some sensitive data in your organization that you want to protect or obscure to prevent illegitimate exploitation? If the answer is YES, you should be in the buyer’s queue of DDM and it will guarantee that your data is safe and it will never come to black hat people. For example, in the banking sector, the bank account/credit card number (in the monthly statement report) or contact number (in the online portal) is masked to prevent its unlawful uses. Similarly, in the health care domain, the list of health ailments associated with any person is highly sensitive and includes private information and it needs special attention in terms of its granular availability to authorized users. DDM would be the right choice to control the availability of data in the original form or fictitious form to the user. DDM has a comprehensive capability to mask data of various relational databases like Oracle, DB2, Sybase, Informix and Teradata.
A use case discussion: Consider this scenario: Organization XYZ wants to mask the original data for the Salary & SSN # columns of the employee table and the returned result set should contain some fictitious values for these two columns.
In order to achieve this masking, a rule can be configured in DDM via a simplified user interface provided by DDM. When DDM intercepts any request that has a reference to the Employee table and requests salary & SSN information, the request will be modified with the configured rules and the result set returned from the database has masked values for both of these columns (highlighted with the yellow color in following diagram).
Rule-set for above use case: - replace salary column data with 9999999999 and SSN# with XXX, for each row of the table.
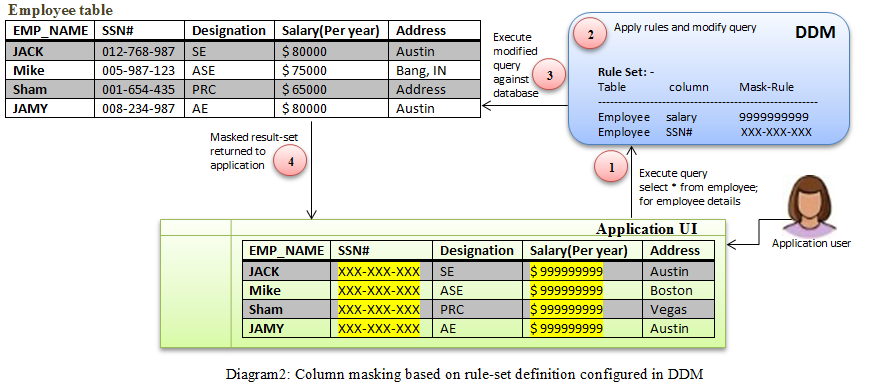 The above diagram shows that the application user executes a select query for employee details, which is intercepted by DDM. DDM modifies the select request by applying the configured rule-set and forwards the request to the database. The database executes the modified query and sends the masked result-set to the application user. The data masking can also be achieved based on the logged in user or the application user. At the bottom of the post, find the DDM rule setup video tutorial and the DDM official document for detailed understanding.
The above diagram shows that the application user executes a select query for employee details, which is intercepted by DDM. DDM modifies the select request by applying the configured rule-set and forwards the request to the database. The database executes the modified query and sends the masked result-set to the application user. The data masking can also be achieved based on the logged in user or the application user. At the bottom of the post, find the DDM rule setup video tutorial and the DDM official document for detailed understanding.
Before concluding this article, it requires a special mention, along with DML statements, DDM also supports stored program unit (procedure, function) masking. Applications can execute procedures or functions stored in the database (let’s say an Oracle database) and the masked result set can be retrieved from the cursor, object or table. The support of stored procedure or function masking differentiates DDM from other masking solutions.
For any organization, data is an invaluable asset and its protection is as important as growth of business. Sometimes the volume of data flow across systems governs the success of the business, but it is our responsibility to prevent sensitive data access from unauthorized users. Informatica, a leading data security solution provider, bestows an efficient and lightweight masking product which guarantees data security for various relational databases.
Official references:-
- Video tutorial- Rule setup and data masking demonstration.
- Official document – Dynamic data masking Admin guide







