Importance of Data Security in Master Data Management
Last Published: Dec 23, 2021 |

How Data Security and MDM work together
Intelligent data-driven disruption is at the forefront of corporate strategies. Using data to capture new opportunities requires a strategic focus on business-critical data. Many companies across a multitude of industries carrying out a variety of business-led initiatives around customer experience, compliance, efficiency, and growth are turning to Master Data Management(MDM). This is the reason MDM continues to draw lots of attention. So, it only goes to say that it's crucial that organizations keep their master data secure.
Accurate data is the lifeblood of innovation and market success. Let's take customer data as an example - a prevalent type of data managed by an MDM program. MDM solutions allow companies to bridge across fragmented silos of customer data and create a trusted customer profile and ultimately deliver differentiated customer experiences.
To keep customers happy and deliver the experiences they expect, companies need to understand customers better. The information about customers is managed in an MDM system and includes many customer attributes. These often include a customer’s name, address, phone numbers, email address, contact preferences, etc. MDM may also store extremely sensitive customer information ranging from Social Security Numbers, Driver’s License Numbers, Account Numbers, and other personally identifiable information(PII).
When there is no MDM solution in place, the risk profile for the organization is higher because sensitive data is distributed across systems. The organizational exposure to certain types of business risk, such as critical information loss and access to unauthorized information, can rapidly spread out of proportion. The thought of having this information fragmented across spreadsheets, local databases, and many on-premises and cloud applications is scary. It is equally frightening to persist this data in your MDM system if you do not have appropriate data security controls in place. If data is the lifeblood, MDM is the heartbeat, with data constantly moving in and out of the MDM system, providing vital information across the whole of your enterprise.
What this means is, before launching an MDM initiative, organizations must develop a comprehensive strategy, which includes a focus on master data security for both data in motion and data at rest. To unleash the full power of MDM throughout their organizations, it is incumbent for companies to rethink traditional methods to cyber/perimeter security approaches; by placing a special focus on the application and the data to ensure they are kept safe, secure and reliable.
Three data security apects companies must consider when evaluating MDM
In the next section, I will discuss the three data security aspects that companies must consider as part of their MDM evaluation.
(1) LEVERAGE THE APPLICATION SECURITY PROVIDED BY YOUR MDM SOFTWARE
1. User Authentication
Authentication is the process of verifying the identity of a user. A user of an MDM solution can be any human or application that requires access to data stored in the MDM system. Ex: A data steward, a line-of-business user, an application used by customer service representative, a kiosk that lets customers order an item from the store, etc.
These users and systems are authenticated based on their supplied credentials, such as a user name and password, or a security payload. The MDM solution must include a well-built internal user authentication management protocol to ensure the user or application is a valid before providing access to the data. In many cases, the authentication system in MDM needs to seamlessly integrate your organization’s existing security systems such as Microsoft Active Directory, Kerberos, etc.
2. User Authorization
Authorization is the process of determining whether a user has sufficient privileges to access a requested data from MDM. The user authorization capability within an MDM solution allows you to secure various resources in the MDM system by enabling only the users with appropriate privileges to gain authorized to access the data. This can be further enhanced by creating role-based user authorizations and access to those resources that are needed to complete the tasks allowed by the user.
3. Access Logs and Timestamps
Organizations should expect their MDM solutions to provide an audit trail and time stamp capabilities. You should see who requested or accessed which MDM records, when and where. These, in turn, should trigger alerts and workflows to flag aberrant behavior.
MDM must time stamp every attribute creation and update. This enables the publication and enforcement of service level agreements (SLAs) for this data. Making credit risk decisions, delivering balance information, or vetting applicants against external lists all rely on current access to the most recent version of the data. A comprehensive MDM solution must provide timestamp information on every attribute in the repository, and provide rules-based business process management capabilities to change query results dynamically, as determined by the age of data. In fact, that capability should be leveraged in weighting trust factors on aging data.
2) INCORPORATE DATA CENTRIC SECURITY WITH ‘DETECT AND PROTECT’:
Assess, Remediate and Monitor Sensitive Data Risks
On a continuous basis, organizations should analyze, remediate and monitor the risks of the sensitive data that will be used in an MDM deployment:
1. Understanding where sensitive data assets reside in the source systems, MDM repository, and target application environments. Use advanced discovery and analytics to determine data sensitivity, location, function, and proliferation.
2.Analyze and prioritize sensitive data risk. Leverage automated risk scoring to determine risk by organizational policy and relevant regulations, how data is used and by whom, as well as how data is moving within the organization.
3. Remediate risk with data security controls. Apply encryption, masking, tokenization and access controls to ensure only those with a need-to-know designation can view data and, in general, limit the access to data by any single individual.
4. Monitor data access. Be mindful of excessive access, cross-border movement, alert on policy, and monitor users for excessive or unusual access with user behavior analytics.
5. Continuously repeat the process one to four. This ensures new data, data stores, and users are analyzed and tracked for risk conditions.
(3) WORK WITH YOUR CHIEF INFORMATION SECURITY OFFICER (CISO)/SECURITY TEAM FOR CYBER-SECURITY
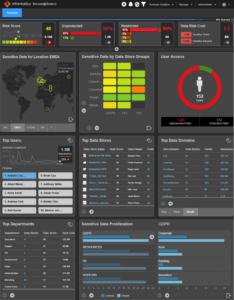 Many organization have invested millions, if not billions, of dollars in security solutions. Your organization’s information security team can determine what legacy controls (such as VPN, firewalls, and SEIMs) will provide visibility to cyber-attacks or malware in your MDM environment.
Many organization have invested millions, if not billions, of dollars in security solutions. Your organization’s information security team can determine what legacy controls (such as VPN, firewalls, and SEIMs) will provide visibility to cyber-attacks or malware in your MDM environment.
Protection and security of your data are important whether it resides on premise, on the cloud, or on hybrid environments. The data management platform you choose should provide you the performance, reliability, and security at its core to project your most valuable asset. Ensure your data management vendor has certifications, assessments, and industry standards in place to protect and safeguard your data in the cloud. You can visit trust.informatica.com to know more about best-in-class data protection.
Because master data is business-critical, comprehensive data security capabilities are paramount for an effective MDM competency. If your MDM is at risk, your entire business is at risk. So, it is important to ensure your MDM vendor supports these comprehensive security approaches that include application, data centric and cyber security controls; without impeding the delivery time and value of your entire MDM project. If you do not focus on this as a priority during your tool selection process, there’s a risk of exposing your data to security and privacy threats. You will also limit your ability to gain the payback from the MDM initiative and may lead to severe consequences for your company’s reputation.
Prash Chandramohan @mdmgeek Robert Shields, CISSP








