“We take privacy and security very seriously. Every data analysis, report and solution we develop needs to be validated for GDPR compliance by our legal and security teams. With Informatica, we’ve gained the visibility and control over our data to meet the regulatory requirements.”
Informatica is named a Leader
The Gartner® Magic Quadrant™ for D&A Governance Platforms marks its first-ever release.
Explore these features
Access governed data that fuels AI and analytics
Gain visibility into data sources and AI models for trusted insights to support explainable and responsible AI.
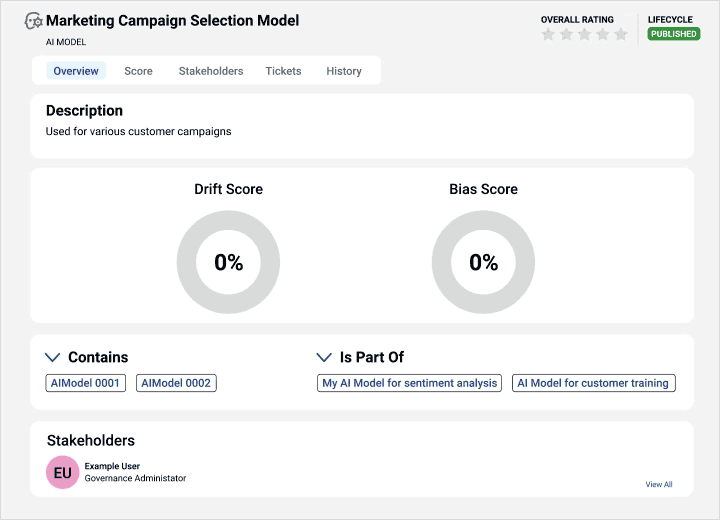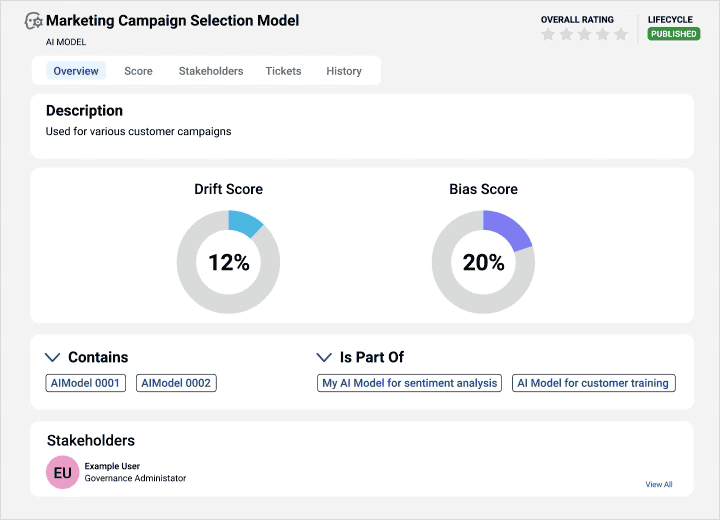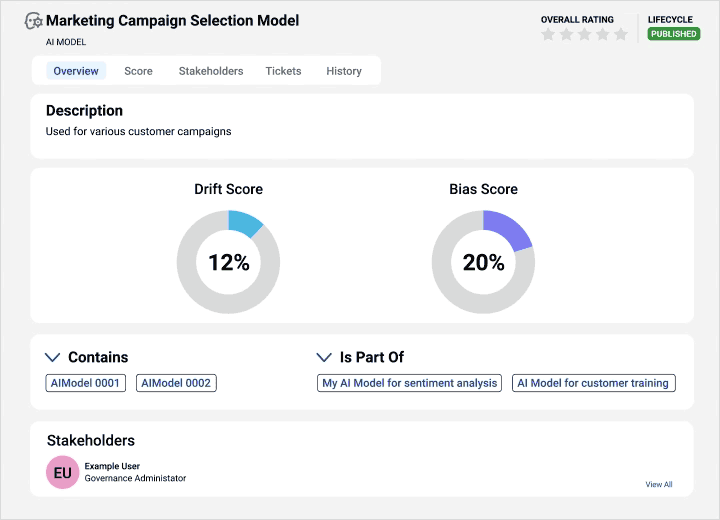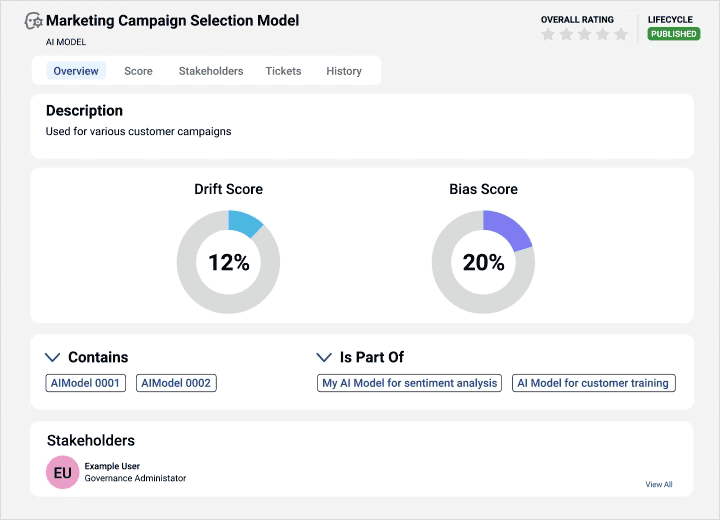
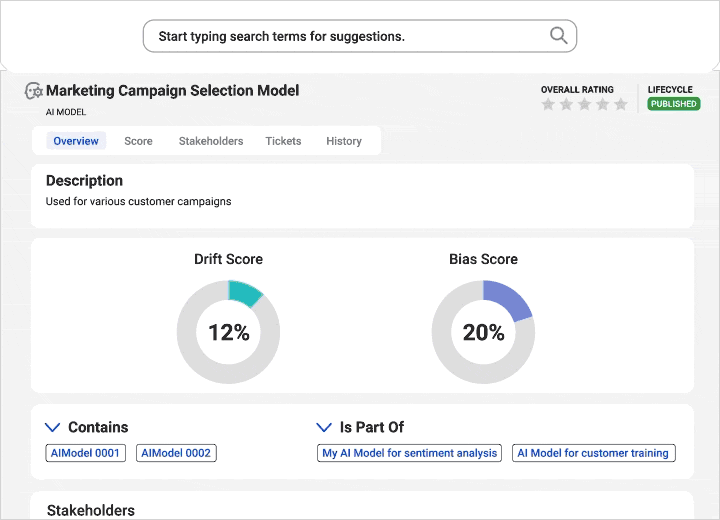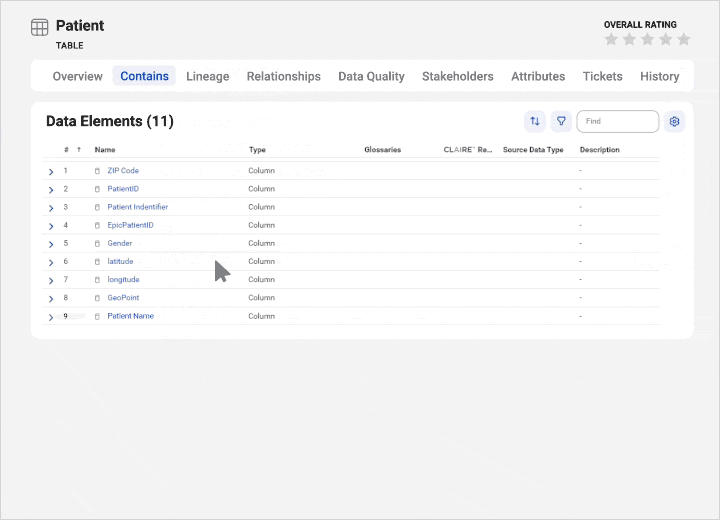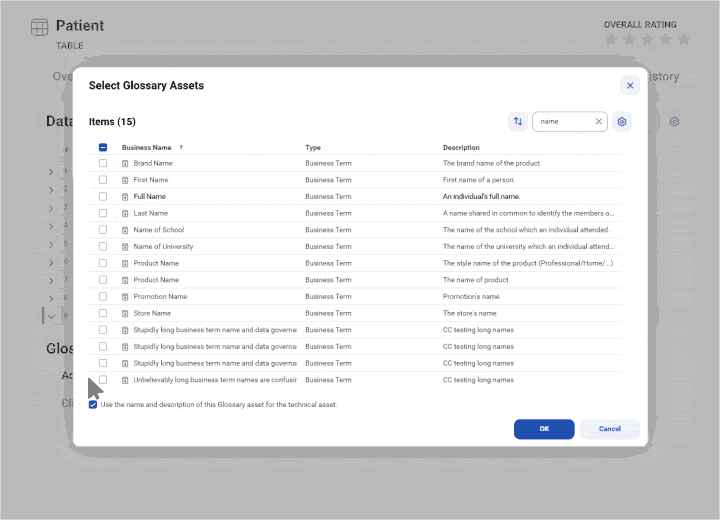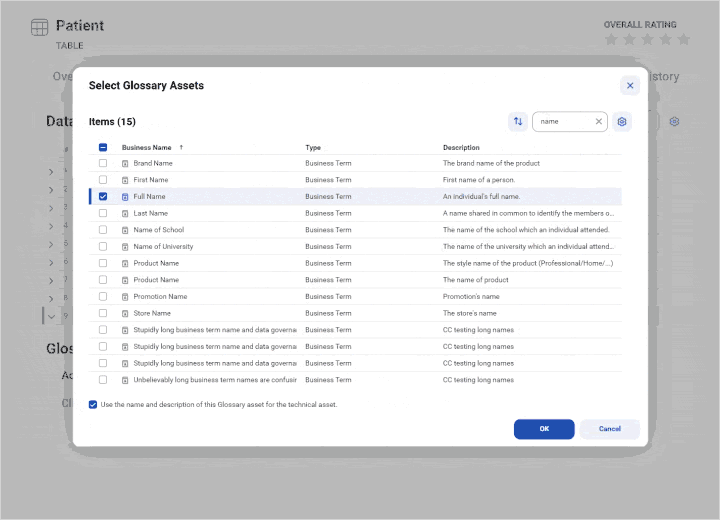
Align business and technical users on data strategy
Automatically link metadata with business context for a holistic view with greater transparency.
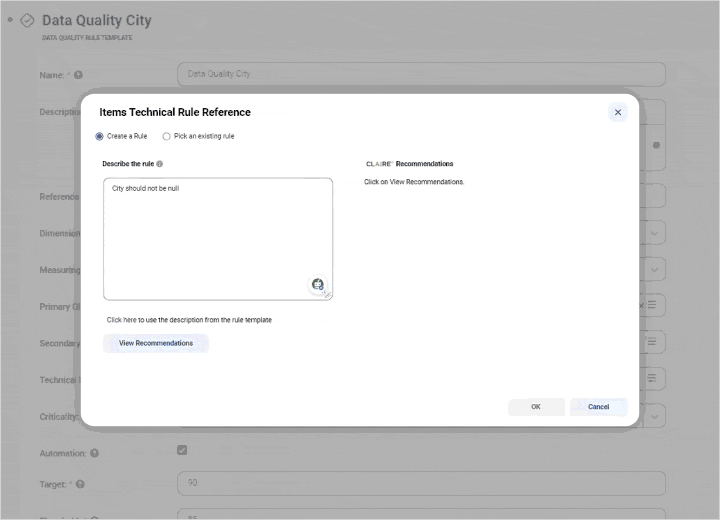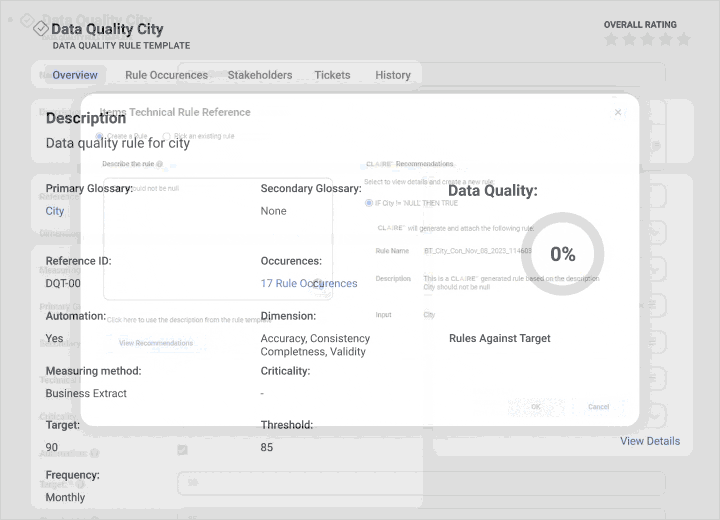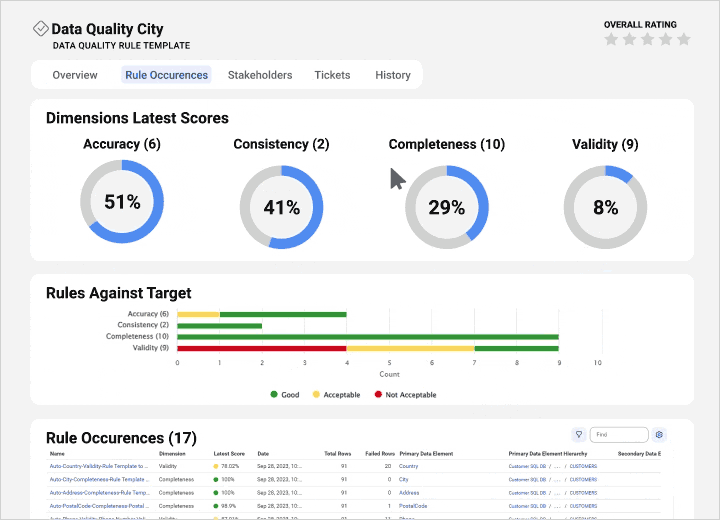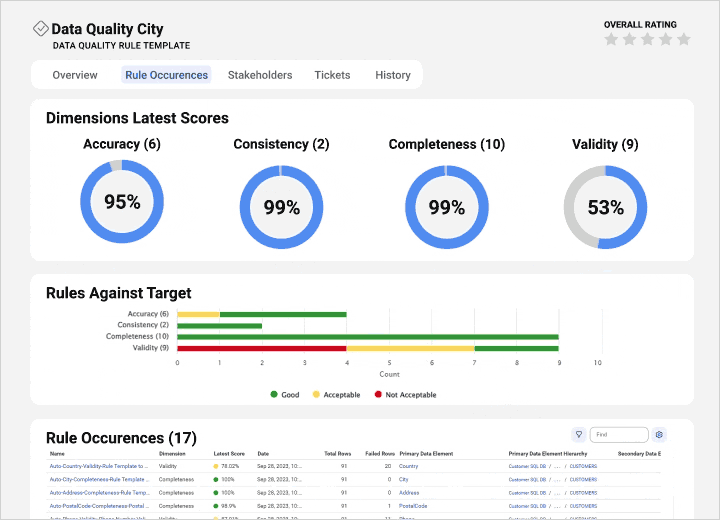
Integrate data quality and observability
View profiling statistics and monitor scorecards from a single pane to improve data quality and insights.
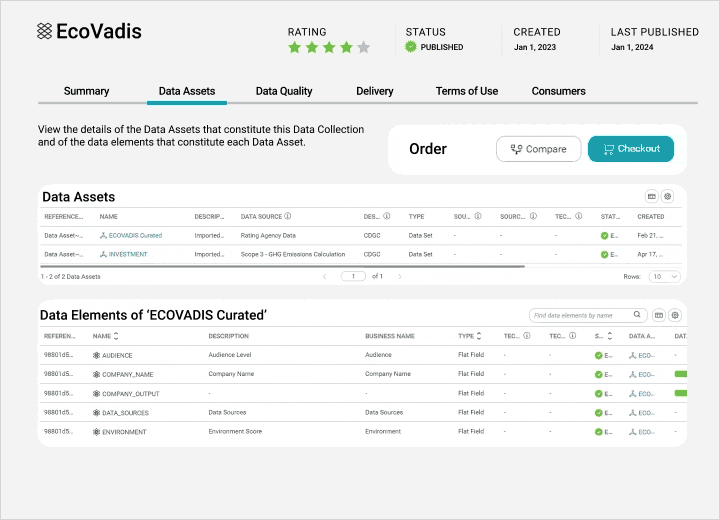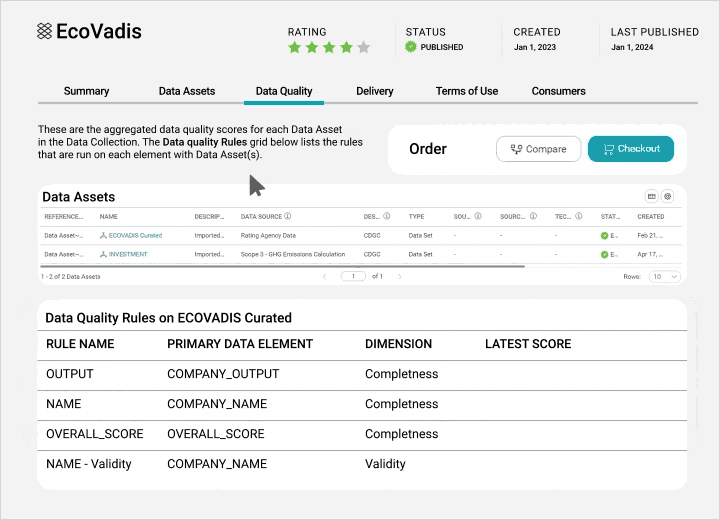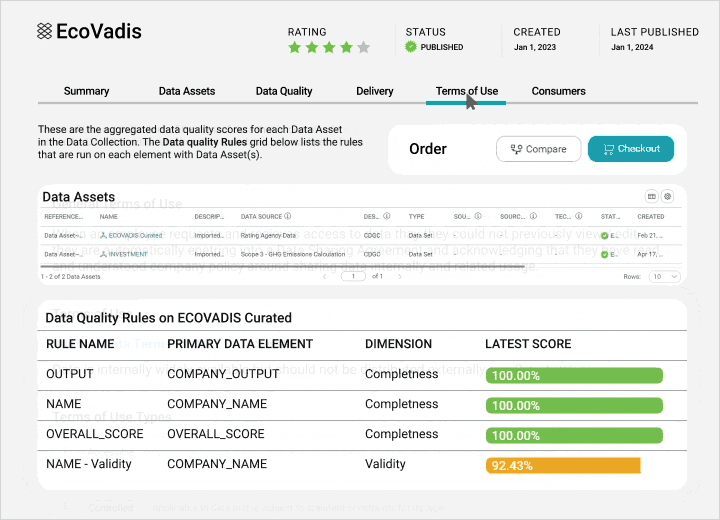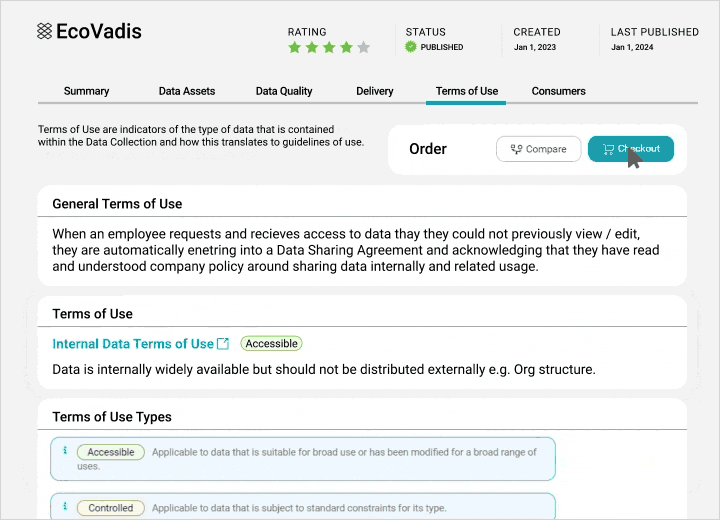
Share data confidently across organizations
Make data available through a governed marketplace to business users, applying policy-based access for safe use.
CLAIRE AI-powered intelligence and automation to accelerate results
Leverage active metadata to simplify data governance processes, increase efficiency and deliver trusted data faster.
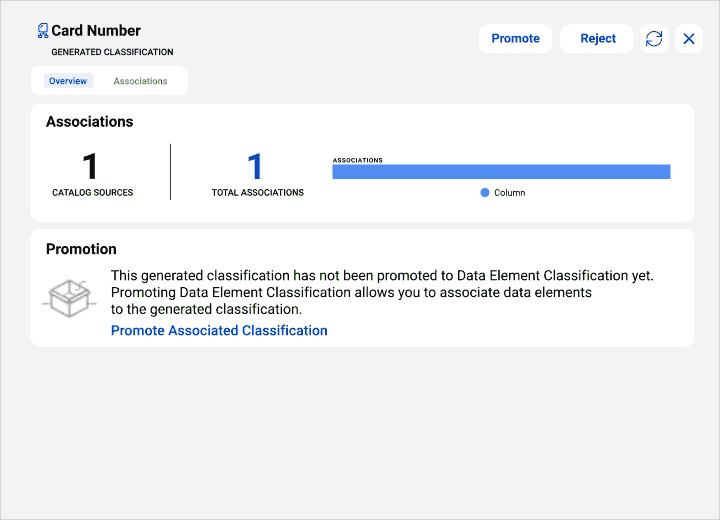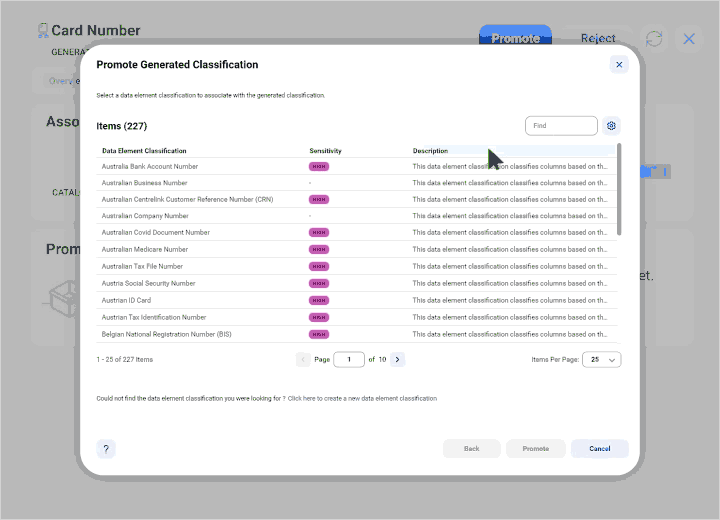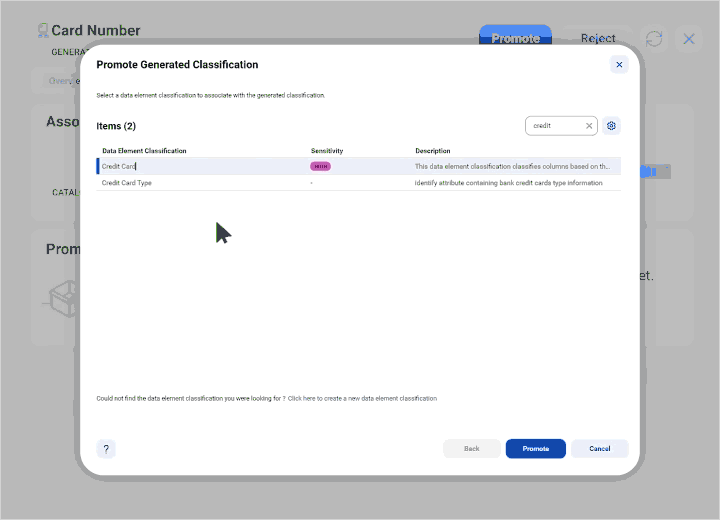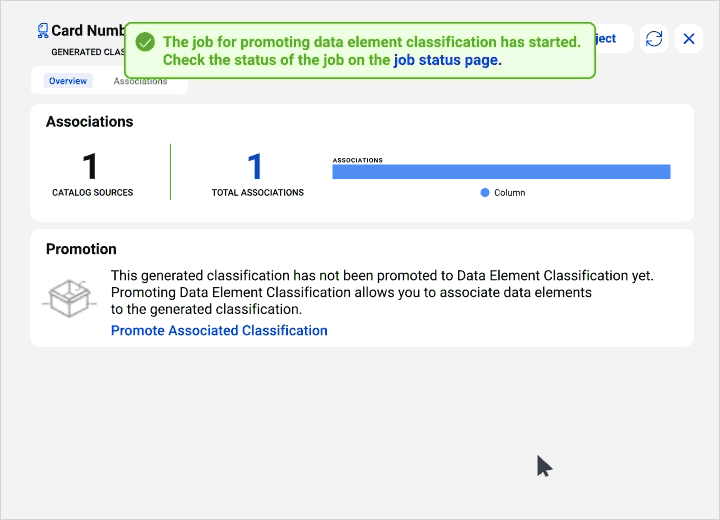
Expand as your business needs grow with access to broad data governance
services at your fingertips.
Enable modern data governance
As a leading part of the AI-powered Informatica Intelligent Data Management Cloud (IDMC), Data Governance & Privacy works with a range of complementary services.
Seamless connection through APIs and extensive scanners
APIs and a broad collection of off-the-shelf and custom scanners provide interoperability with third-party systems.
Essential Data Governance resources
Modern Data Governance for CDOs

data sheet

Analyst Report
Informatica Named Leader in Gartner® Magic Quadrant™ for Data & Analytics Governance Platforms

Workbook
Deliver Data Intelligence with Cloud Data Governance and Catalog

GUIDE
AI Governance for Dummies

FAQs about Data Governance
Data governance is a set of principles, standards and practices to help ensure your data is reliable, consistent, and trustworthy. It involves establishing frameworks with policies and procedures that guide the creation, use and maintenance of data safely, securely and responsibly.
Data governance drives business value creation by enabling: Trusted analytics and AI with improved data quality; efficient, transparent and reliable business reporting and compliance; increased transparency and collaboration between business and IT users; data literacy and a shared understanding of data; healthy data pipelines for analytics and AI, and more.
When choosing a data governance tool, key factors include AI-enabled automation, scalability, seamless integration with existing systems, ease of use, customizability, robust vendor support and cost considerations.
Start by identifying critical business drivers and pain points to achieving trusted data. Identify current and desired data transparency and align program goals with your organization’s data strategy. Begin with a small, achievable pilot project that delivers high ROI results data stakeholders care about and showcase the value of your pilot program to build support and scale out.











