Data Security vs Data Privacy—What’s the Difference
Last Published: Sep 24, 2025 |

,With Data Privacy Day here once again, you may be asking yourself two common questions:
- “Aren’t data security and data privacy the same thing?”
- “How are data privacy and data security different?”
A quick search online appears to often intertwine the two topics, so let’s have some fun with a short quiz to test your perspective.
Data Security and Data Privacy Quiz
Which of these recommendations would you characterize as a data security or data privacy best practice?
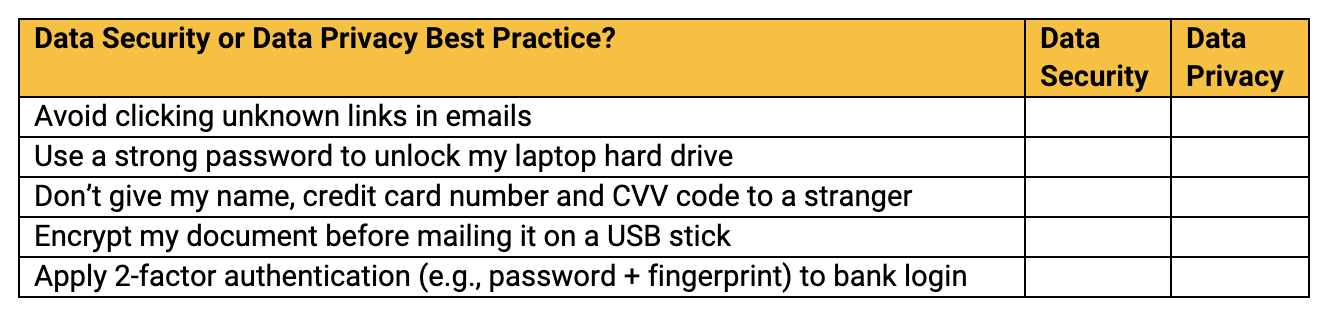
How did you do?
Check your answers:
If you answered, “data security” to each question, you might be right
BUT
If you answered, “data privacy” to each question, you might also be right
Yeah, it’s complicated.
Data Security vs. Data Privacy – Let’s Compare
“Data security” is often defined as being an access control problem to manage, while “data privacy” is usually defined as being a data governance policy for moderating a data exposure problem. Why is that?
Data Security
Just like the lock that guards your door, data security tends to be a more black-and-white, definitive, control for determining access. For example:
- Either you can access data on your company’s server, or you cannot.
- Either your data is in the hands of “trusted employees” or it’s been hacked by “the bad actors” (not Nicholas Cage, sorry—more like malicious foreign governments).
- Either the data is encrypted so that only “authorized” (approved) users can unlock it to use it, or it’s in cleartext (unencrypted), and anyone can access it, without restriction.
Data Privacy
Data privacy, on the other hand, tends to be more nuanced around controlling the gray area of limiting data exposure to abuses or misuse, and has a lot to do with policies that define the context or circumstances of enabling appropriate data use:
- I am entitled to access customer data, but should it be used to fuel my affinity marketing program?
- Data is used by trusted data stewards, but does my customer approve of it being shared with others?
- Sensitive data is encrypted, but what attributes are needed to be seen for effective customer service?
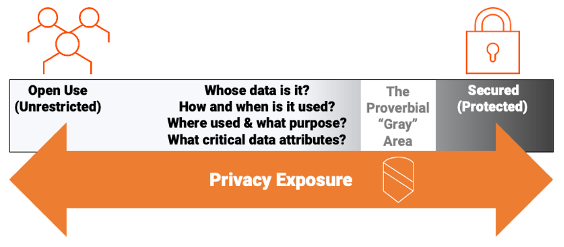
These two areas are certainly related: Data security can be an effective control that protects data access, but between the two extremes of open access and locked-down protection, data privacy is that gray area in-between that moderates and governs data exposure and considers the risks to data use.
“Data Privacy” helps answer a fundamental question: If I am authorized to have access to secured data, is the data exposed appropriately and used in alignment with the policies of the data owner, data user, and any other stakeholders?
Going back to our quiz, let’s see if we can better differentiate these activities below for more clarity with regard to a data security best practice vis-à-vis a data privacy one.
Can we better assess the context of data use as it differentiates to solving data privacy concerns?
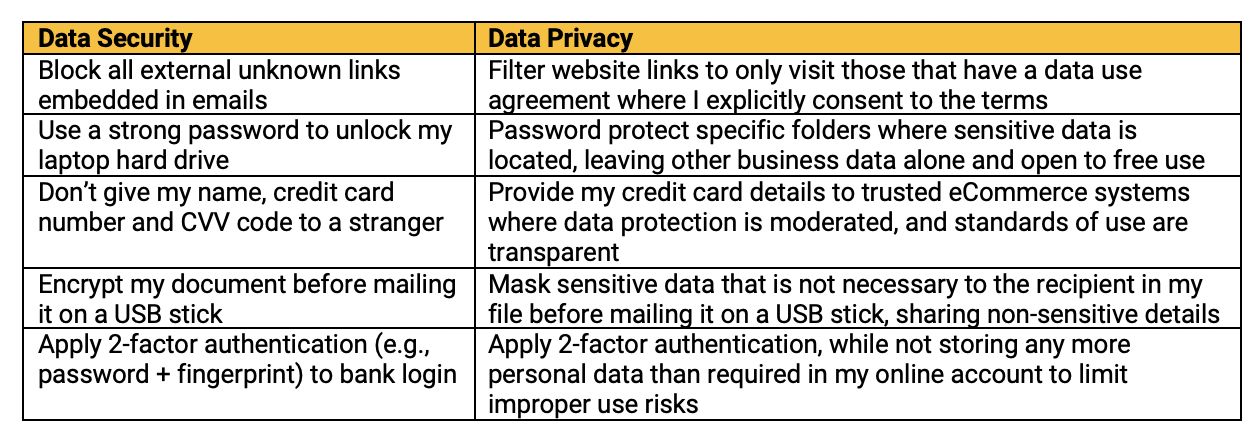
The Criticality of Data Security vs. Data Privacy: The Proverbial Gray Area
As you saw from the earlier graphic, there is a gray area that focuses primarily on context of use and that’s where data privacy mostly applies, since there is no perfect answer between the security scope of data locked down (unusable) vs. data without security controls (in the clear).
It’s a matter of data risk exposure:
- Are your data governance controls strong and effective enough to limit data exposure that protects confidentiality to a reasonable degree?
- Are your policies, at minimum, aligned with the data owner’s expectations for data use?
- Are all data stakeholders willing to risk the expected data value creation opportunities against potential abuses to data exposure that could harm trusted relationships?
Today there are a myriad of new data privacy mandates, from the GDPR, to the CCPA, to LGPD, PDPA, and beyond. These mandates are intended primarily to protect consumer privacy (i.e., data exposure) by requiring personal data protection and consumer approval for how the data is being used. And, in addition to requiring strong data security controls, there’s also an accountability to supporting privacy rights with transparency into how data is used to further align policies with expectations.
While security tools such as data encryption or data masking can help protect data privacy, they require data privacy governance for intelligent decision making to determine whether exposure is appropriate (and when the exposure is not appropriate, how to fix it!).
Data privacy governance helps enable:
- Enforcement of data use policies that reflect the standards of due care agreed upon between data users and owners, and other stakeholders, of that sensitive data
- Classification and cataloging of sensitive data to determine what’s in scope and subject to various privacy mandates, such as personal information
- Mapping identities with data to monitor and respond to routine inquiries that measure privacy policies, such as data subject access requests (DSARs) that can include, “whose data is used, how, and where?”
- Data privacy risk analytics to measure whether exposure is appropriate according to the data privacy policies being defined and enforced, and
- If data risk exposure is misaligned, enable remediation, such as security controls to protect data, or to take actions that impact data retention or reduce risks through data minimization
- And finally, auditing and reporting to determine gaps in data privacy controls, improve policies, and respond to inquiries that prove data use can be trusted
Data Privacy Governance: The key to applying security effectively to govern privacy
Informatica addresses both sides of the coin for security and privacy, offering security technologies such as persistent data masking, dynamic data masking, and related technologies to anonymize and pseudonymize data by reducing the sensitive data attributes exposed in records and files. Rather than purely encrypting data and files to make them unusable, data masking is more nuanced by limiting data privacy exposure through conditional use that reflects best-practice policies.
However, going one step further, Informatica’s data privacy governance solutions that bring together policy controls, data discovery and classification, identity mapping, risk analytics and remediation, and auditing and reporting on a single, consistent platform are able to apply security controls more effectively using automation, AI, and metadata intelligence to drive expected behavior. It’s like having an invisible hand to help toe that fine line between opportunity vs. risk. Here’s why…
Implementing Data Privacy Benefits Both Companies and Their Consumers Alike
Instead of locking down data to secure it from any and all exposure, data privacy governance applies metadata intelligence and automated controls to help ensure that personal and sensitive data is used appropriately. And that’s something we can all agree on!
Companies can derive more intelligence from their consumers to develop and improve products and services, creating more stickiness and loyalty—and consumers receive a customized user experience within the scope of their privacy rights, enabled by trust.
Organizations can feel confident when applying security controls for privacy to democratize data use—safely—and unleash more business value across the enterprise, while complying with global privacy mandates. A win-win scenario.
Learn More from Industry Experts
- View our Data Governance and Privacy Summit now available on demand








